User Logon
Enabled by default
Service: syslog
Log type: auth.log
A users log in will likely be the first sign of an attack and can indicate suspicious behavior. It can also give an analyst a starting time to create a timeline of events. This log is required in the HIPAA and PCI DSS regulations.
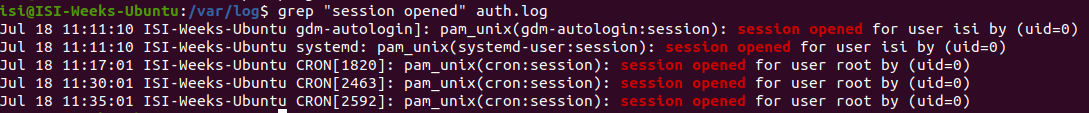
grep "session opened" /var/log/auth.log
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Compliance
HIPAA
Level: Recommended
PCI DSS
Level: Required
https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2-1.pdf?agreement=true&time=1631643252599
NSA Event Forwarding
Level: Recommended
https://github.com/nsacyber/Event-Forwarding-Guidance/tree/master/Events
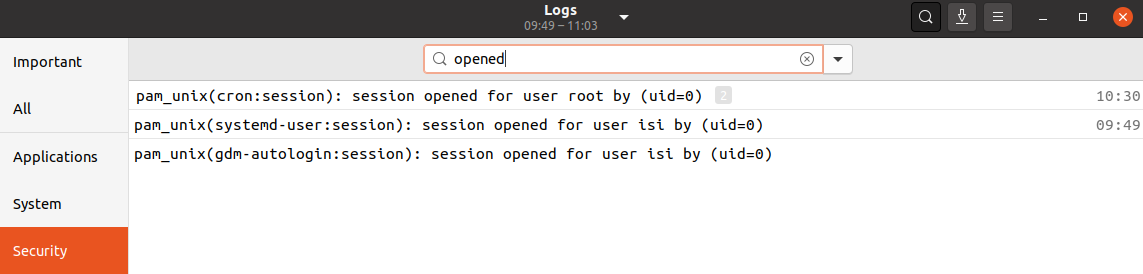
Linux logs call a user login event session opened. There may be logs from a “user” called GDM; this is just the graphical login screen and will show up if a user switched accounts graphically. In order to view this event from the Logs application, select the Security tab and search for opened.
To view this log through the command line, launch the terminal and enter the command grep "session opened" /var/log/auth.log.