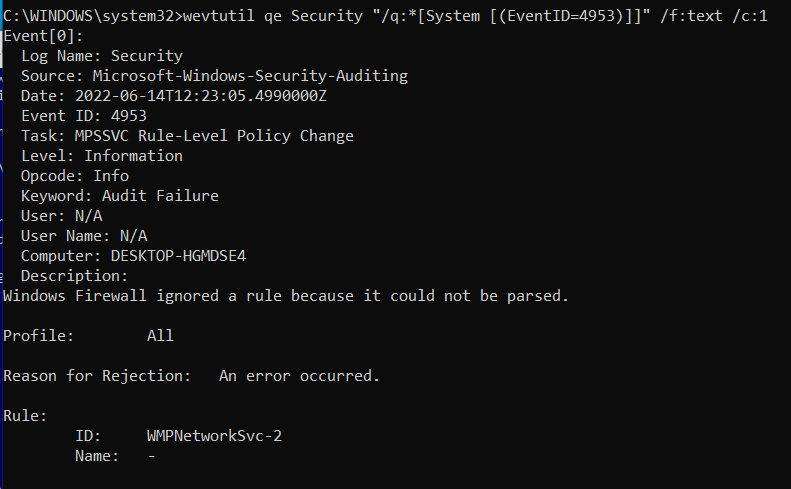
Windows Firewall Rule Ignored Due to Parsing Issue
Enabled by default
Service: Microsoft Windows security auditing
Log type: Security
There are two Event Logs that indicate that Windows Firewall has not parsed a rule. This one is particularly important as it means that a rule is set up incorrectly and that Windows Firewall can not use it. This is an indication that a rule may need to be fixed.
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4953'} -MaxEvents 1 | Format-Listauditpol /get /subcategory:"MPSSVC Rule-Level Policy Change"
auditpol /set /subcategory:"MPSSVC Rule-Level Policy Change" /Success:Disable /Failure:Disable
auditpol /set /subcategory:"MPSSVC Rule-Level Policy Change" /Success:Enable /Failure:Enable
Windows 10 does not log this by default. To enable logging of this activity, launch the Group Policy Editor. From here, expand the Windows Logs folder and open the Security Settings tab. Then, Expand the Advanced Audit Policies - Local Group Policy tab and then the System Audit Policies- Local Group Policies tab. Then navigate to the Policy Change tab.
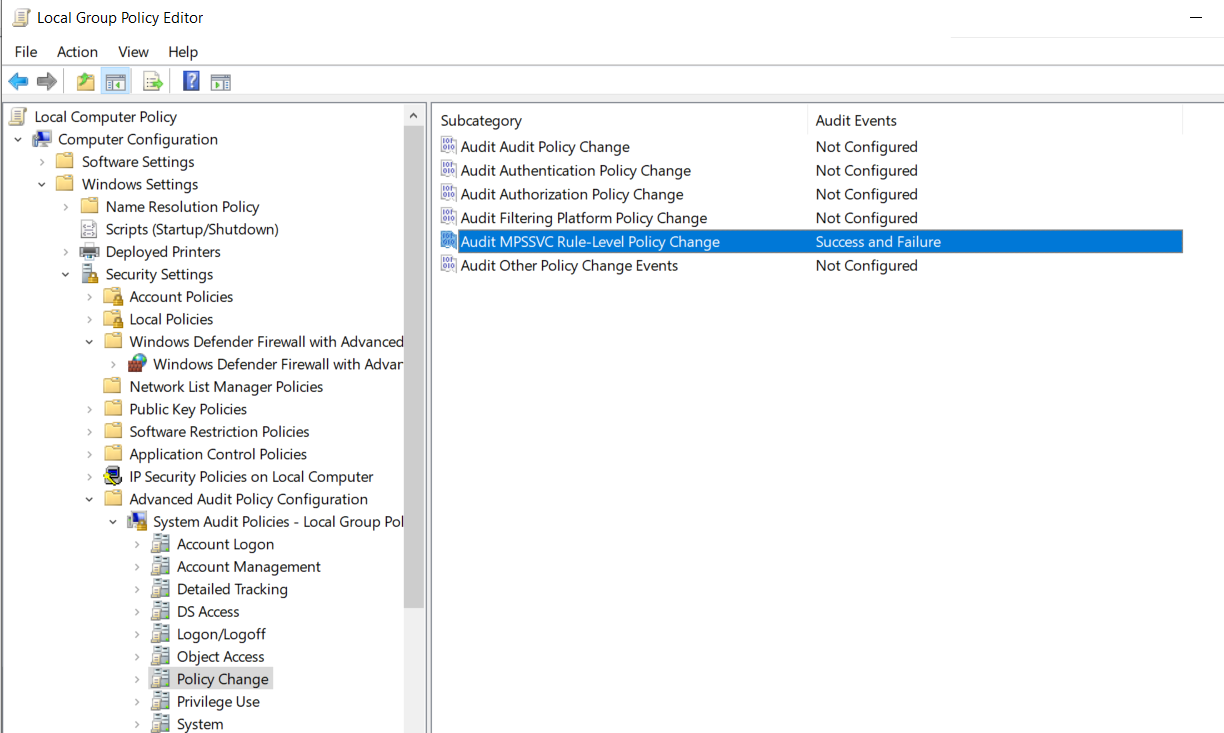
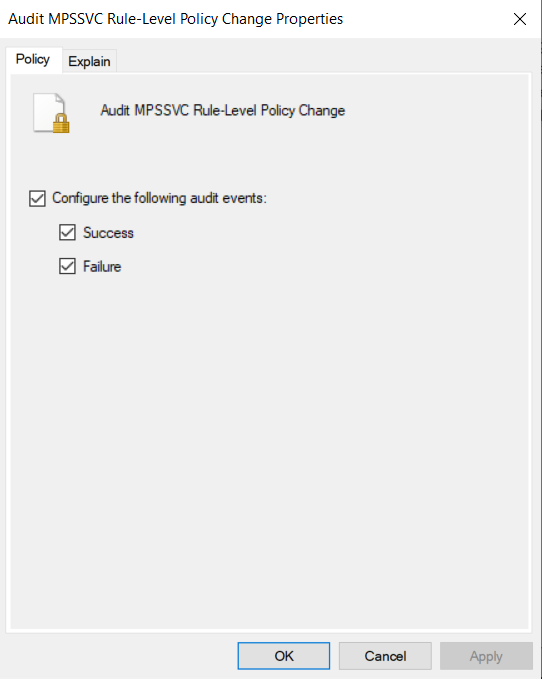
In the Policy Change tab, double click on the Audit MPSSVC Rule-Level Policy Change selection and select Success and Failure. This will turn on auditing for Firewall Policy events.
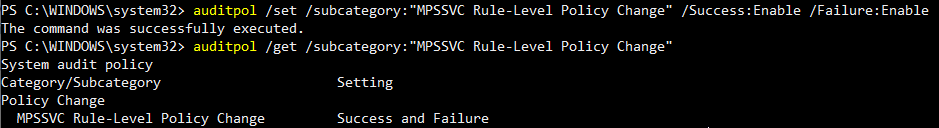
Windows 10 does not log this by default. To enable logging of this activity, launch Powershell as an admin. Then, to enable logging, enter the command auditpol /set /subcategory:"MPSSVC Rule-Level Policy Change" /Success:Enable /Failure:Enable
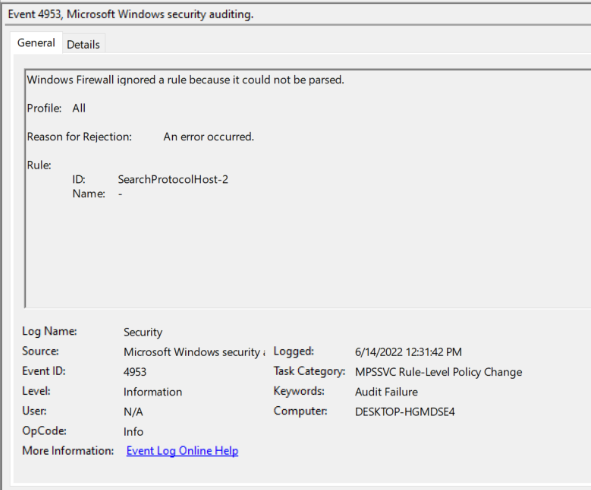
To view this log in the Event Viewer, open the event viewer and navigate to the Windows Logs heading and then the Security Tab. From here, select the find function and search for the value 4953 , or filter the log for the ID 4953.
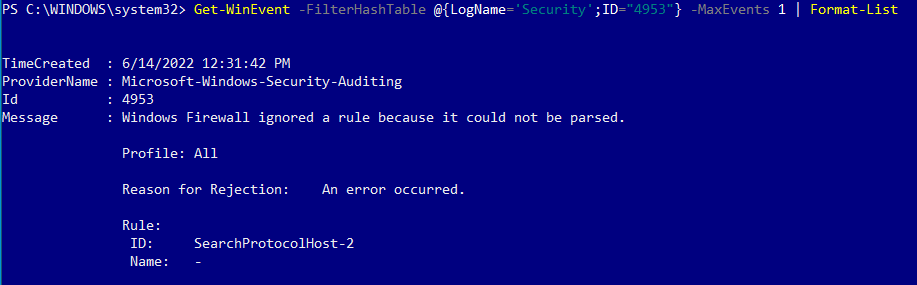
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Security';ID='4953'} -MaxEvents 1 | Format-List
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe Security "/q:*[System [(EventID=4953)]]" /f:text /c:1