Software Installed
Enabled by default
Service: Microsoft Windows security auditing.
Log type: Application
Many attacks rely on software being installed and this log can signal who and what installed the software that may cause a vulnerability. It can also be used to make sure that only authorized apps are being installed.
Get-WinEvent -FilterHashTable @{LogName='Application';ID='11707'} -MaxEvents 1 | Format-ListUnfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Compliance
Changes made to a security group are automatically logged and can be viewed in the application tab of the Event Viewer. However, it is important to note windows only logs events that are done through the MsiInstaller in this log. To view these logs, sort or filter by event ID 11707.
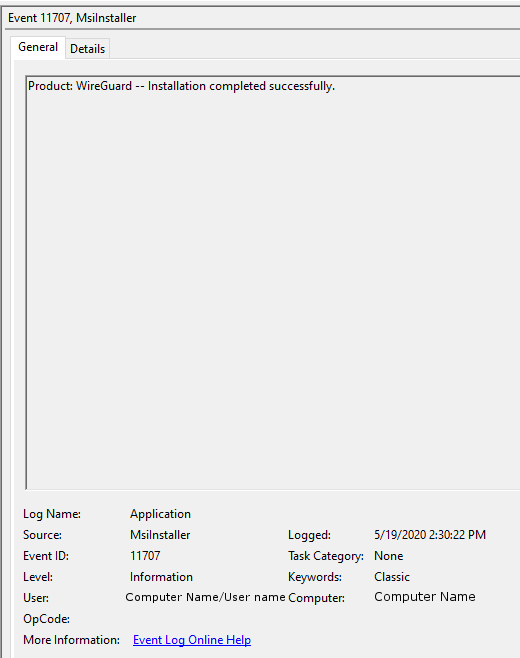
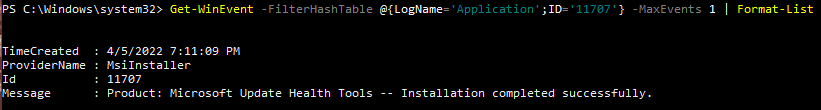
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Application';ID='11707'} -MaxEvents 1 | Format-List
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe Application "/q:*[System [(EventID=11707)]]" /f:text /c:1

Additional References
https://docs.microsoft.com/en-us/windows/win32/msi/event-logging
