Account Created
Windows Event ID: 4720
Enabled by default
Service: Microsoft Windows Security auditing
Log type: Security
Account creation logs can indicate a suspicious new account that was created in preparation for an attack or someone trying to do things they necessarily shouldn’t. It is also a good idea to know when there may be new users on the network so you are prepared for their activity. This log is required by NIST SP 800-53, HIPAA and PCI DSS regulations. It is also recommended under the NSA Cyber Event Forwarding Guidance.
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4720'}auditpol /get /subcategory:"computer account management"
auditpol /set /subcategory:"computer account management" /Success:Disable /Failure:Disable
auditpol /set /subcategory:"computer account management" /Success:Enable /Failure:Enable
Compliance
PCI DSS
Level: Required
https://www.pcisecuritystandards.org/document_library?category=pcidss&document=pci_dss
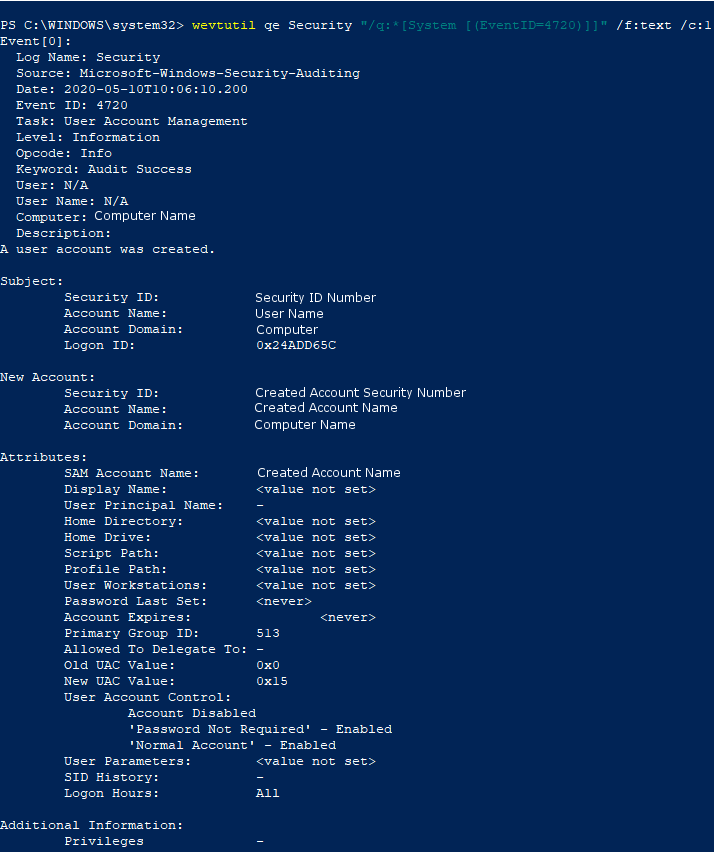
Windows 10 Professional logs this by default. To view, navigate to the security tab of the Windows Event Viewer. Sort or filter the logs for event ID 4720.
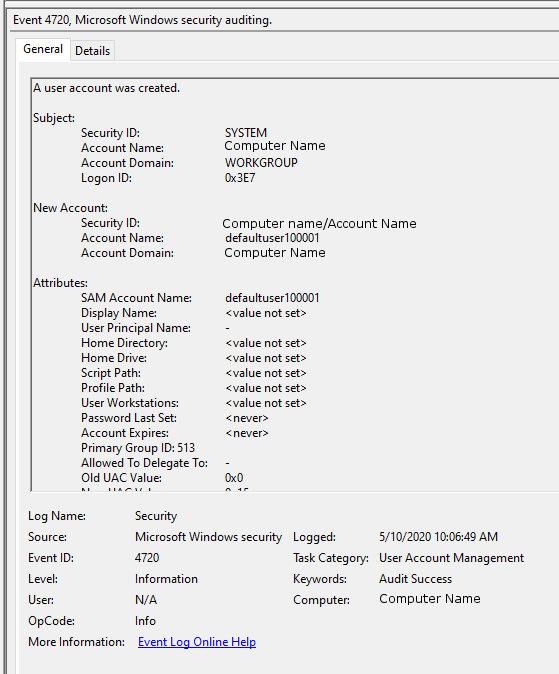
To view this log in the command line with Get-WinEvent, run powershell as an administrator. Enter the command Get-WinEvent -FilterHashTable @{LogName='Security';ID='4720'}
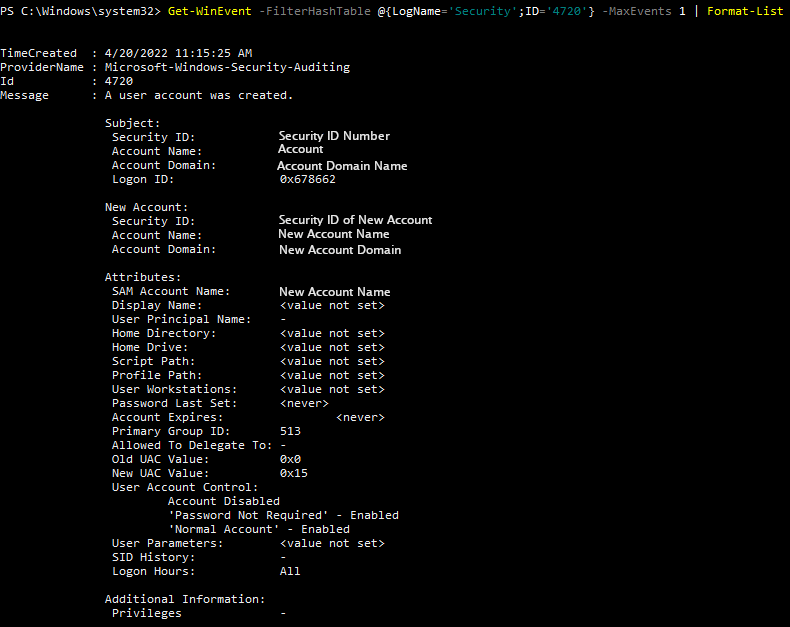
To view this log in the command line with wevt, run the command prompt or powershell as an administrator. Enter the command wevtutil qe Security "/q:*[System [(EventID=4720)]]"