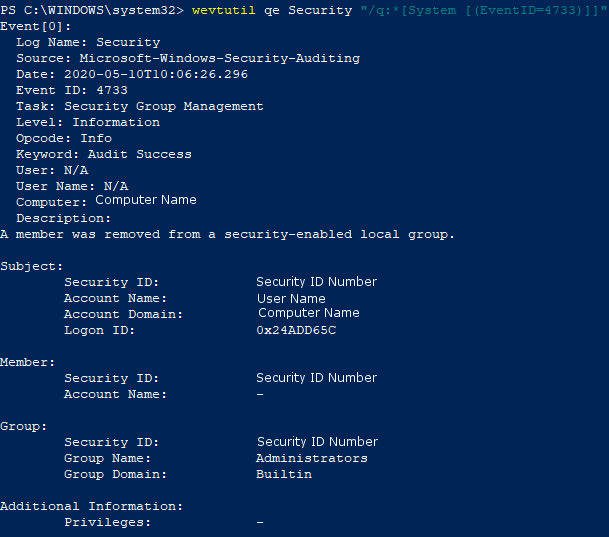
Member Removed from Group
Enabled by default
Service: Microsoft Windows Security auditing
Log type: Security
Group membership change can indicate a user removing themselves from an admin group in an effort to clean up after an attack. It is important to monitor the groups that have escalated permissions.
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4733'} -MaxEvents 1 | Format-Listauditpol /get /subcategory:"security group management"
auditpol /set /subcategory:"security group management" /Success:Disable /Failure:Disable
auditpol /set /subcategory:"security group management" /Success:Enable /Failure:Enable
Compliance
HIPAA
Level: Recommended
NSA Event Forwarding
Level: Recommended
https://github.com/nsacyber/Event-Forwarding-Guidance/tree/master/Events
Windows 10 Professional logs group membership changes by default. To view this log, navigate to the Event Viewer security tab. To view the log of a member being removed from a group, sort or filter by the IDs 4733.
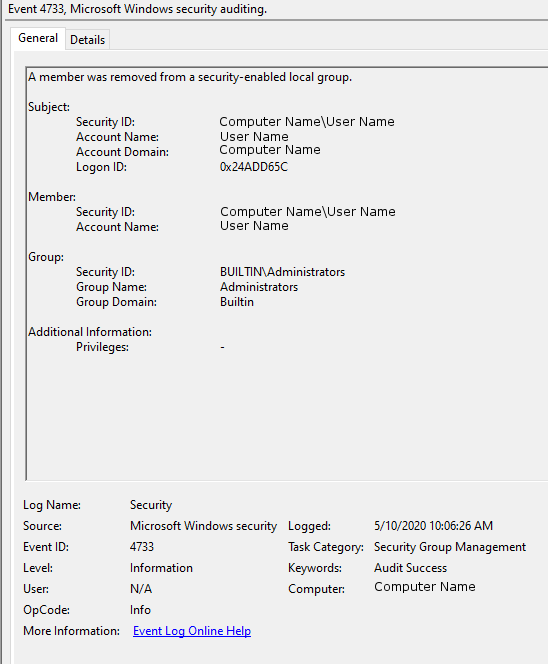
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Security';ID='4733'} -MaxEvents 1 | Format-List
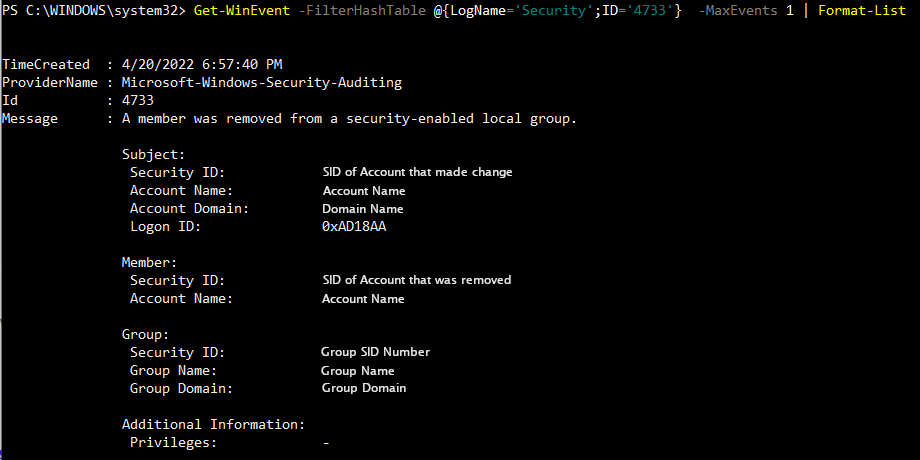
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the command wevtutil qe Security "/q:*[System [(EventID=4733)]]"