Process Creation
Enabled by default
Service: Microsoft Windows Security auditing
Log type: Security
While applications being opened is a common occurrence on a computer, this log allows you to see if there were unusual applications being opened. This log allows you to identify if unauthorized or malicious applications were opened.
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4688'} -MaxEvents 1 | Format-Listauditpol /get /subcategory:"Process Creation
auditpol /set /subcategory:"Process Creation" /Success:Disable /Failure:Disable
auditpol /set /subcategory:"Process Creation" /Success:Enable /Failure:Enable
Compliance
HIPAA
Level: Recommended
PCI DSS
Level: Recommended
https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2-1.pdf?agreement=true&time=1631643252599
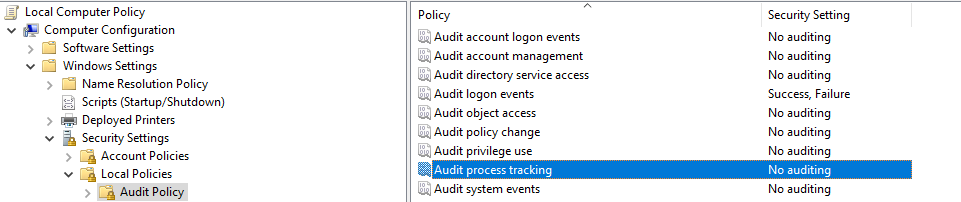
By default, process creation is not logged in Windows 10 professional and has to be turned on in the Group Policy Editor. To do so, navigate to the audit policy tab under local policies, security settings, and the windows settings folder. Select audit process tracking, as shown in the photo.
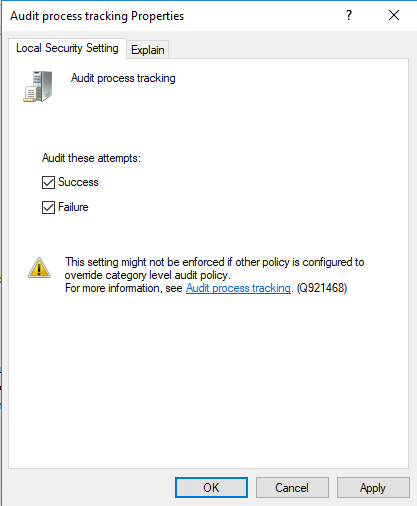
Click on the check box next to success in order to ensure that process creation is logged. Then click Apply and Ok to close the pop-up window and apply the change. To ensure the audit policy is updated to incorporate these changes, in a command prompt, enter
Gpdupdate /force
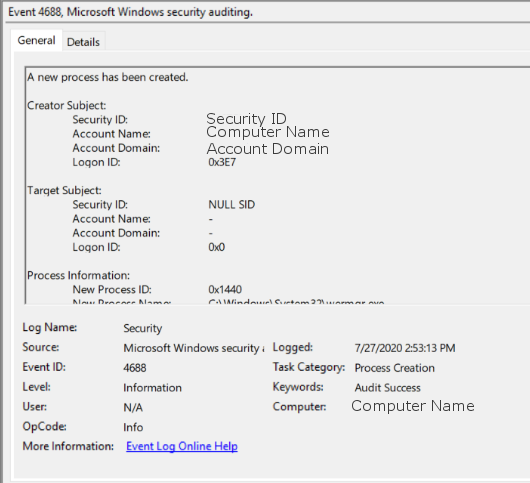
To view the process creation log, navigate to the Windows Event Viewer and the security tab. Next, sort or filter the log by Event ID 4688.
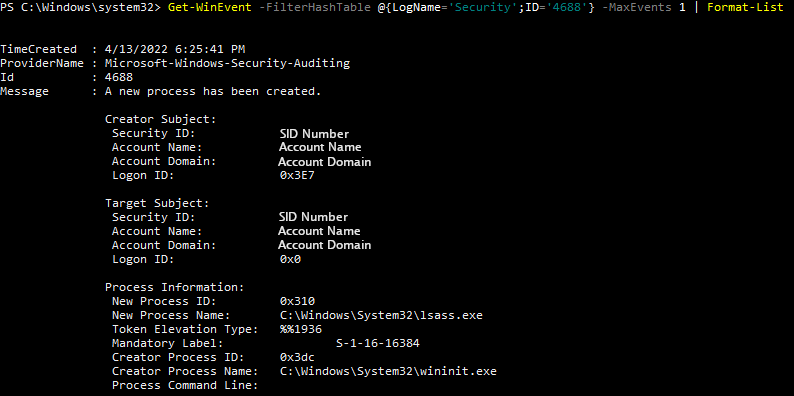
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Security';ID='4688'} -MaxEvents 1 | Format-List
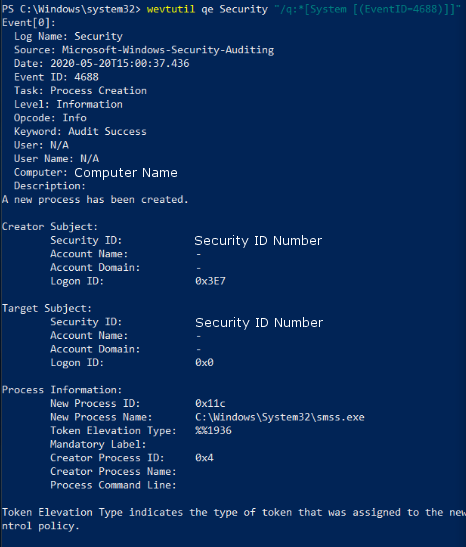
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe Security "/q:*[System [(EventID=4688)]]"