Service Installed
Enabled by default
Service: Service Control Manager
Log type: System
Services on a Windows machine have many purposes and these logs may indicatea malicious service being placed on the computer, such as a virus or other malware. This log is recommended by JPCERTCC.
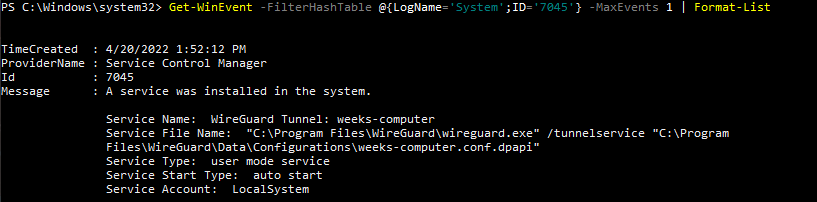
Get-WinEvent -FilterHashTable @{LogName='System';ID='7045'} -MaxEvents 1 | Format-ListUnfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Compliance
Service Installation is not automatically logged by Windows 10 and needs to be turned on in the group policy editor. To turn on the audit security system extension properties, navigate to the group policy editor. Then, go Computer Configuration > Windows Settings > Advanced Audit Policy Configuration > System Audit Policies-Local Group > System.
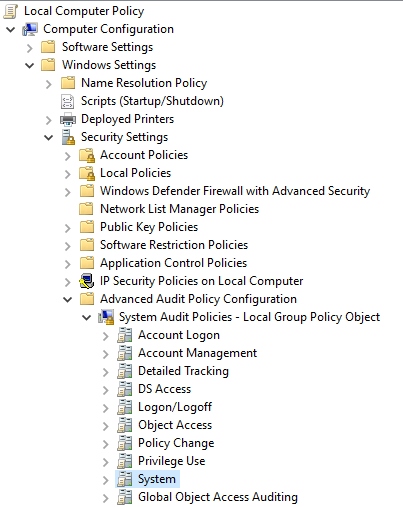
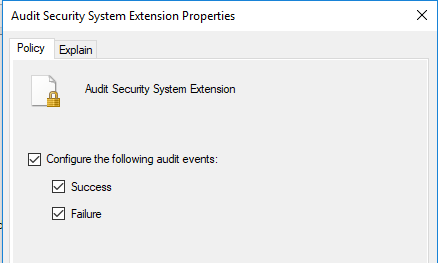
Finally, click on Audit Security System Extension and select the check boxes. Then click Apply and Ok to save and apply the changes. To ensure the audit policy is updated to incorporate these changes, in a command prompt, enter Gpdupdate /force
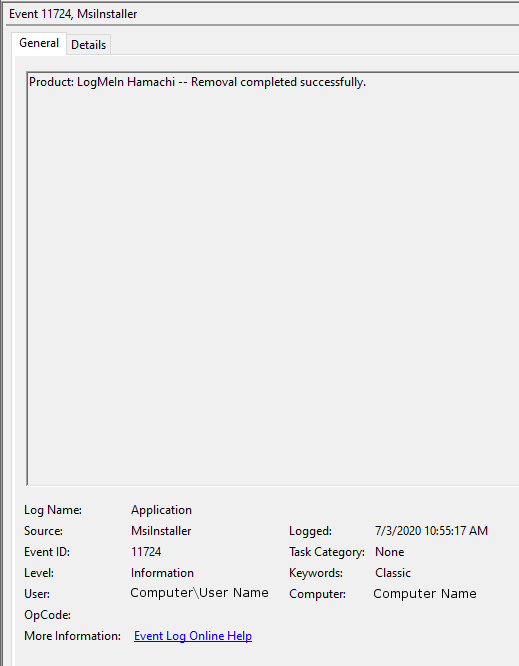
To view this log, enter the Event Viewer as an administrator and navigate to the Security tab. Sort or filter the logs by Event ID 7045.
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='System';ID='7045'} -MaxEvents 1 | Format-List
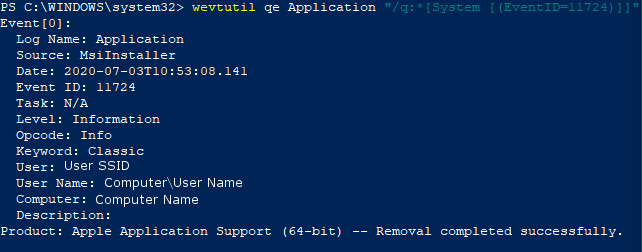
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe System "/q:*[System [(EventID=7045)]]"