Software Updated
Enabled by default
Service: Service Control Manager
Log type: System
Software updates are not always a sign of an attack, but often contain patches for known vulnerabilities. An update may also introduce vulnerabilities and it is important to know if and when that was installed.
Get-WinEvent -FilterHashTable @{LogName='Application';ID='1036';ProviderName='MsiInstaller'} -MaxEvents 1 | Format-ListUnfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Unfortunately, due to current limitations, we do not yet have this command, stay tuned for updates!
Compliance
HIPAA
Level: Recommended
https://www.hipaajournal.com/patch-update-computer-software-face-hipaa-sanction/
PCI DSS
Level: Recommended
https://www.hipaajournal.com/patch-update-computer-software-face-hipaa-sanction/
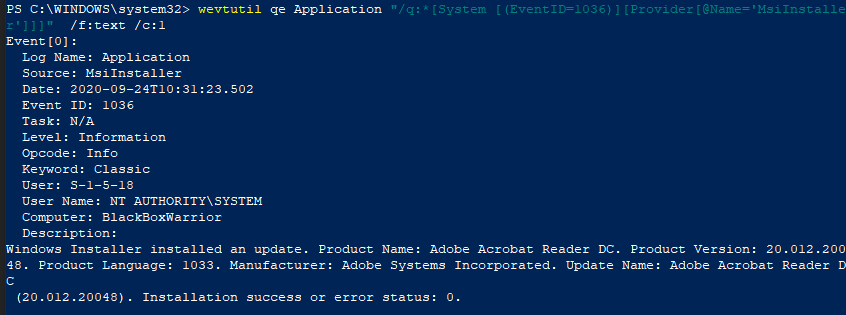
Software updates that are performed through MsiInstaller are automatically logged and can be viewed in the application tab of the Event Viewer. With this log, there is an ID conflict with another application. To view this log, select Filter Current Log and select the Event Sources as MsiInstaller and with the event ID 1036.
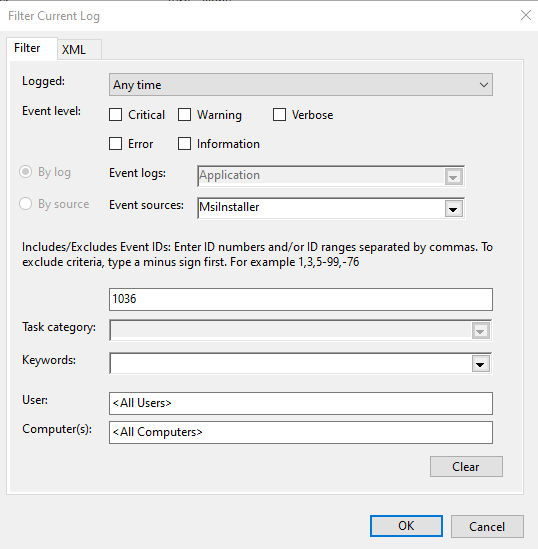
The image will look like this:
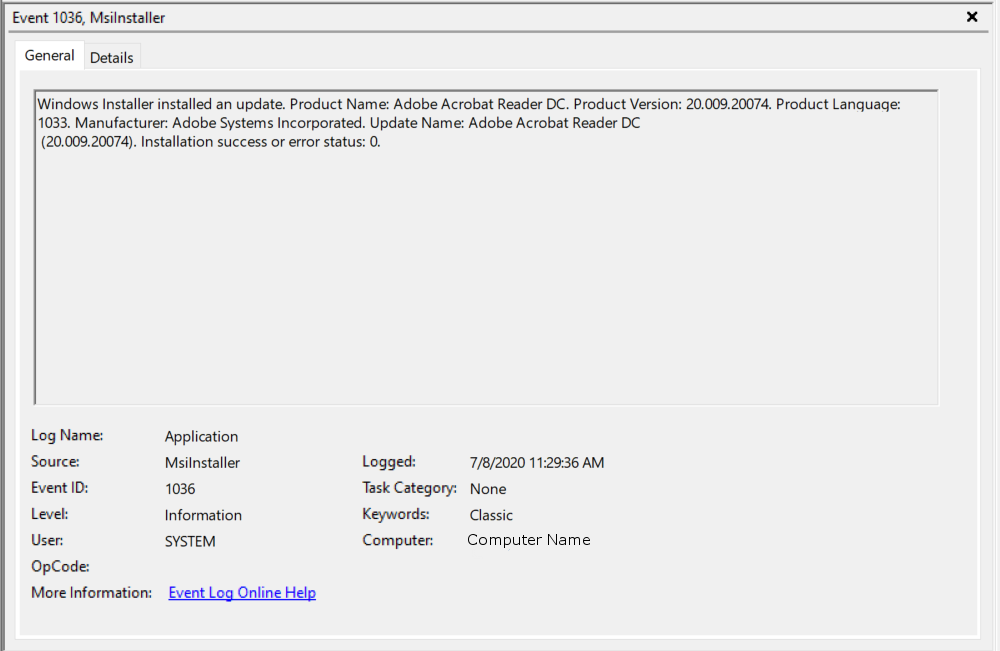
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Application';ID='1036';ProviderName='MsiInstaller'} -MaxEvents 1 | Format-List
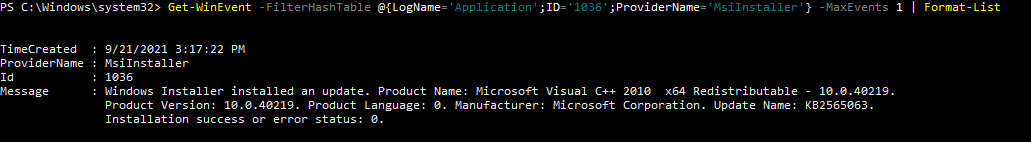
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe Application "/q:*[System [(EventID=1036)][Provider[@Name='MsiInstaller']]]" /f:text /c:1